Session Initiation Protocol
| Internet protocol suite |
|---|
| Application layer |
| Transport layer |
| Internet layer |
| Link layer |
The Session Initiation Protocol (SIP) is a communications protocol for signaling and controlling multimedia communication session such as voice and video calls. The most common applications of SIP are in Internet telephony, as well as instant messaging, over Internet Protocol (IP) networks.
The protocol defines the messages that are sent between endpoints, which govern establishment, termination and other essential elements of a call. SIP can be used for creating, modifying and terminating sessions consisting of one or several media streams. SIP is an application layer protocol designed to be independent of the underlying transport layer. It is a text-based protocol, incorporating many elements of the Hypertext Transfer Protocol (HTTP) and the Simple Mail Transfer Protocol (SMTP).[1]
SIP works in conjunction with several other application layer protocols that identify and carry the session media. Media identification and negotiation is achieved with the Session Description Protocol (SDP). For the transmission of media streams (voice, video) SIP typically employs the Real-time Transport Protocol (RTP) or Secure Real-time Transport Protocol (SRTP). For secure transmissions of SIP messages, the protocol may be encrypted with Transport Layer Security (TLS).
History
SIP was originally designed by Mark Handley, Henning Schulzrinne, Eve Schooler and Jonathan Rosenberg in 1996. The protocol was standardized as RFC 2543 in 1999. In November 2000, SIP was accepted as a 3GPP signaling protocol and permanent element of the IP Multimedia Subsystem (IMS) architecture for IP-based streaming multimedia services in cellular networks. In June 2002 the specification was revised in RFC 3261[2] and various extensions and clarifications have been published since.[3]
The protocol was designed with the vision to support new multimedia applications. It has been extended for video conferencing, streaming multimedia distribution, instant messaging, presence information, file transfer, fax over IP and online games.[4][5][6]
SIP is distinguished by its proponents for having roots in the Internet community rather than in the telecommunications industry. SIP has been standardized primarily by the IETF, while other protocols, such as H.323, have traditionally been associated with the International Telecommunication Union (ITU).
Protocol operation
SIP can be carried by several transport layer protocols including the Transmission Control Protocol (TCP), the User Datagram Protocol (UDP) or the Stream Control Transmission Protocol (SCTP).[7] SIP can be used to establish two-party (unicast) or multiparty (multicast) sessions.
SIP employs design elements similar to the HTTP request/response transaction model.[8] Each transaction consists of a client request that invokes a particular method or function on the server and at least one response. SIP reuses most of the header fields, encoding rules and status codes of HTTP, providing a readable text-based format.
Each resource of a SIP network, such as a user agent or a voicemail box, is identified by a uniform resource identifier (URI), based on the general standard syntax also used in Web services and e-mail.[9] The URI scheme used for SIP is sip and a typical SIP URI has the form sip:username@domainname or sip:username@hostport, where domainname requires DNS SRV records to locate the servers for SIP domain while hostport can be an IP address or a fully qualified domain name of the host and port.[10][11] If secure transmission is required, the scheme sips is used.
SIP works in concert with several other protocols and is only involved in the signaling portion of a communication session. SIP clients typically use TCP or UDP on port numbers 5060 or 5061 to connect to SIP servers and other SIP endpoints. Port 5060 is commonly used for non-encrypted signaling traffic whereas port 5061 is typically used for traffic encrypted with Transport Layer Security (TLS). SIP is primarily used in setting up and tearing down voice or video calls. It also allows modification of existing calls. The modification can involve changing addresses or ports, inviting more participants, and adding or deleting media streams. SIP has also found applications in messaging applications, such as instant messaging, and event subscription and notification. A suite of SIP-related Internet Engineering Task Force (IETF) rules define behavior for such applications. The voice and video stream communications in SIP applications are carried over another application protocol, the Real-time Transport Protocol (RTP). Parameters (port numbers, protocols, codecs) for these media streams are defined and negotiated using the Session Description Protocol (SDP), which is transported in the SIP packet body.
A motivating goal for SIP was to provide a signaling and call setup protocol for IP-based communications that can support a superset of the call processing functions and features present in the public switched telephone network (PSTN). SIP by itself does not define these features; rather, its focus is call setup and signaling. The features that permit familiar telephone-like operations (i.e. dialing a number, causing a phone to ring, hearing ringback tones or a busy signal) are performed by proxy servers and user agents. Implementation and terminology are different in the SIP world compared to the PSTN but, to the end-user, the behavior is similar.
SIP-enabled telephony networks often implement many of the call processing features of Signaling System 7 (SS7), although the two protocols themselves are very different. SS7 is a centralized protocol, characterized by a complex central network architecture and dumb endpoints (traditional telephone handsets). SIP is a client-server protocol, however most SIP-enabled devices may perform both the client and the server role. In general, the session initiator is a client, and the call recipient is the server. SIP features are implemented in the communicating endpoints, contrary to traditional SS7 architecture, in which features are implemented in the network core.
Because SIP devices must perform both client and server roles, network communication can be difficult with modern network topologies. When using a connection-oriented protocol like TCP, SIP nominally expects that separate connections will be opened for requests from A to B and requests from B to A. The use of firewalls and network address translation (NAT) interferes with this, as it may not be possible for B to initiate a connection to A, if A is behind a firewall or NAT. SIP allows the original connection from A to B to be used for requests from B to A, but the requests must correctly distinguish between A's private and public addresses and ports; this is also true of requests on connectionless protocols like UDP. To accomplish this, SIP uses extensions like received and rport,[12] and can be paired with other protocols for discovering network topology such as TURN, STUN, and ICE.
Network elements
SIP defines user agents as well as several types of server network elements. Two SIP endpoints can communicate without any intervening SIP infrastructure. However, this approach is often impractical for public services, which need directory services to locate available nodes in the network.
User agent
A SIP user agent (UA) is a logical network end-point used to create or receive SIP messages and thereby manage a SIP session. A SIP UA can perform the role of a user agent client (UAC), which sends SIP requests, and the user agent server (UAS), which receives the requests and returns a SIP response. Unlike other network protocols where the roles of client and server are fixed (e.g., a web browser only acts as an HTTP client, and never acts as an HTTP server), in SIP requests can go in either direction, so in almost all cases, a SIP UA must be capable of performing both roles. (If a SIP UA could only perform one role, it could only receive calls and have calls hung up by the peer, but not make calls or hang them up itself, or vice versa.) These roles of UAC and UAS only last for the duration of a SIP transaction.[5]
A SIP phone is an IP phone that implements client and server functions of a SIP user agent and provides the traditional call functions of a telephone, such as dial, answer, reject, call hold, and call transfer.[13][14] SIP phones may be implemented as a hardware device or as a softphone. As vendors increasingly implement SIP as a standard telephony platform, the distinction between hardware-based and software-based SIP phones is blurred and SIP elements are implemented in the basic firmware functions of many IP-capable devices. Examples are devices from Nokia and BlackBerry.[15]
In SIP, as in HTTP, the user agent may identify itself using a message header field User-Agent, containing a text description of the software, hardware, or the product name. The user agent field is sent in request messages, which means that the receiving SIP server can see this information. SIP network elements sometimes store this information,[16] and it can be useful in diagnosing SIP compatibility problems.
Proxy server
The proxy server is an intermediary entity that acts as both a server and a client for the purpose of making requests on behalf of other clients. A proxy server primarily plays the role of routing, meaning that its job is to ensure that a request is sent to another entity closer to the targeted user. Proxies are also useful for enforcing policy, such as for determining whether a user is allowed to make a call. A proxy interprets, and, if necessary, rewrites specific parts of a request message before forwarding it.
Registrar
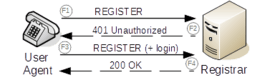

A registrar is a SIP endpoint that accepts REGISTER requests, recording the address and other parameters from the user agent, and that provides a location service for subsequent requests. The location service links one or more IP addresses to the SIP URI of the registering agent. Multiple user agents may register for the same URI, with the result that all registered user agents receive the calls to the URI.
SIP registrars are logical elements, and are commonly co-located with SIP proxies. To improve network scalability, location services may instead be located with a redirect server.
Redirect server
A redirect server is a user agent server that generates 3xx (redirection) responses to requests it receives, directing the client to contact an alternate set of URIs. A redirect server allows proxy servers to direct SIP session invitations to external domains.
Session border controller
Session border controllers serve as middle boxes between UA and SIP servers for various types of functions, including network topology hiding and assistance in NAT traversal.
Gateway
Gateways can be used to interconnect a SIP network to other networks, such as the public switched telephone network, which use different protocols or technologies.
SIP messages
SIP is a text-based protocol with syntax similar to that of HTTP. There are two different types of SIP messages: requests and responses. The first line of a request has a method, defining the nature of the request, and a Request-URI, indicating where the request should be sent.[17] The first line of a response has a response code.
Requests
Requests initiate a SIP transaction between two SIP entities for establishing, controlling, and terminating sessions. Critical methods include the following.
- INVITE: Used to establish a dialog with media exchange between user agents.
- BYE: Terminates an existing session.
- REGISTER: The method implements a location service for user agents, which indicate their address information to the server.
Responses
Responses are sent by the user agent server indicating the result of a received request. Several classes of responses are recognized, determined by the numerical range of result codes:[18]
- 1xx: Provisional responses to requests indicate the request was valid and is being processed.
- 2xx: 200-level responses indicate a successful completion of the request. As a response to an INVITE, it indicates a call is established.
- 3xx: This group indicates a redirection is needed for completion of the request. The request has to be completed with a new destination.
- 4xx: The request contained bad syntax or cannot be fulfilled at the server.
- 5xx: The server failed to fulfill an apparently valid request.
- 6xx: This is a global failure, as the request cannot be fulfilled at any server.
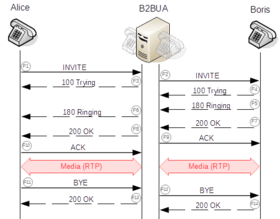
Transactions
SIP defines a transaction mechanism to control the exchanges between participants and deliver messages reliably. A transaction is a state of a session, which is controlled by various timers. Client transactions send requests and server transactions respond to those requests with one or more responses. The responses may include provisional responses, which a response code in the form 1xx, and one or multiple final responses (2xx – 6xx).
Transactions are further categorized as either type Invite or type Non-Invite. Invite transactions differ in that they can establish a long-running conversation, referred to as a dialog in SIP, and so include an acknowledgment (ACK) of any non-failing final response, e.g., 200 OK.
Because of these transactional mechanisms, unreliable transport protocols, such as the User Datagram Protocol (UDP), are sufficient for SIP operation.
Instant messaging and presence
The Session Initiation Protocol for Instant Messaging and Presence Leveraging Extensions (SIMPLE) is the SIP-based suite of standards for instant messaging and presence information. MSRP (Message Session Relay Protocol) allows instant message sessions and file transfer.
Conformance testing
TTCN-3 test specification language is used for the purposes of specifying conformance tests for SIP implementations. SIP test suite is developed by a Specialist Task Force at ETSI (STF 196).[20] The SIP developer community meets regularly at the SIP Forum SIPit events to test interoperability and test implementations of new RFCs.
Performance testing
When developing SIP software or deploying a new SIP infrastructure, it is very important to test capability of servers and IP networks to handle certain call load: number of concurrent calls and number of calls per second. SIP performance tester software is used to simulate SIP and RTP traffic to see if the server and IP network are stable under the call load.[21] The software measures performance indicators like answer delay, answer/seizure ratio, RTP jitter and packet loss, round-trip delay time.
Applications
A SIP connection is a marketing term for voice over Internet Protocol (VoIP) services offered by many Internet telephony service providers (ITSPs). The service provides routing of telephone calls from a client's private branch exchange (PBX) telephone system to the public switched telephone network (PSTN). Such services may simplify corporate information system infrastructure by sharing Internet access for voice and data, and removing the cost for Basic Rate Interface (BRI) or Primary Rate Interface (PRI) telephone circuits.
Many VoIP phone companies allow customers to use their own SIP devices, such as SIP-capable telephone sets, or softphones.
SIP-enabled video surveillance cameras can make calls to alert the owner or operator that an event has occurred; for example, to notify that motion has been detected out-of-hours in a protected area.
SIP is used in audio over IP for broadcasting applications where it provides an interoperable means for audio interfaces from different manufacturers to make connections with one another.[22]
Implementations
The U.S. National Institute of Standards and Technology (NIST), Advanced Networking Technologies Division provides a public-domain Java implementation[23] that serves as a reference implementation for the standard. The implementation can work in proxy server or user agent scenarios and has been used in numerous commercial and research projects. It supports RFC 3261 in full and a number of extension RFCs including RFC 6665 (event notification) and RFC 3262 (reliable provisional responses).
Numerous other commercial and open-source SIP implementations exist. See List of SIP software.
SIP-ISUP interworking
SIP-I, or the Session Initiation Protocol with encapsulated ISUP, is a protocol used to create, modify, and terminate communication sessions based on ISUP using SIP and IP networks. Services using SIP-I include voice, video telephony, fax and data. SIP-I and SIP-T[24] are two protocols with similar features, notably to allow ISUP messages to be transported over SIP networks. This preserves all of the detail available in the ISUP header, which is important as there are many country-specific variants of ISUP that have been implemented over the last 30 years, and it is not always possible to express all of the same detail using a native SIP message. SIP-I was defined by the ITU-T, whereas SIP-T was defined via the IETF RFC route.[25]
Encryption
The increasing concerns about the security of calls that run over the public Internet has made SIP encryption more popular and, in fact more desired.
If secure transmission is required, the sips URI scheme is used and mandates that each hop over which the request is forwarded up to the target domain must be secured with Transport Layer Security (TLS). The last hop from the proxy of the target domain to the user agent has to be secured according to local policies. TLS protects against attackers who try to listen on the signaling link but it does not provide real end-to-end security to prevent espionage and law enforcement interception, as the encryption is only hop-by-hop and every single intermediate proxy has to be trusted.
Because VPN is not an option for most service providers, most service providers that offer secure SIP (SIPS) connections use TLS for securing signaling. The relationship between SIP (port 5060) and SIPS (port 5061), is similar to that as for HTTP and HTTPS, and uses URIs in the form "sips:user@example.com". The media streams, which occur on different connections to the signaling stream, can be encrypted with SRTP. The key exchange for SRTP is performed with SDES (RFC 4568), or the newer and often more user friendly ZRTP (RFC 6189), which can automatically upgrade RTP to SRTP using dynamic key exchange (and a verification phrase). One can also add a MIKEY (RFC 3830) exchange to SIP and in that way determine session keys for use with SRTP.
See also
- Voice over IP
- Rendezvous protocol
- Peer-to-peer SIP
- Computer telephony integration (CTI)
- Computer-supported telecommunications applications (CSTA)
- H.323 protocols H.225.0 and H.245
- IP Multimedia Subsystem (IMS)
- Extensions to the Session Initiation Protocol for the IP Multimedia Subsystem
- Media Gateway Control Protocol (MGCP)
- Message Session Relay Protocol (MSRP)
- Mobile VoIP
- MSCML (Media Server Control Markup Language)
- Network convergence
- RTP audio video profile
- SIGTRAN (Signaling Transport)
- SIP trunking
- SIP provider
- Skinny Client Control Protocol (SCCP)
- XIMSS (XML Interface to Messaging, Scheduling, and Signaling)
- ZRTP
References
- ↑ Johnston, Alan B. (2004). SIP: Understanding the Session Initiation Protocol, Second Edition. Artech House. ISBN 1-58053-168-7.
- ↑ "SIP core working group charter". Ietf.org. 2010-12-07. Retrieved 2011-01-11.
- ↑ "Search Internet-Drafts and RFCs". Internet Engineering Task Force.
- ↑ "What is SIP?". Network World. May 11, 2004.
- 1 2 "RFC 3261 – SIP: Session Initiation Protocol". IETF. 2002.
- ↑ Margaret Rouse. "Session Initiation Protocol (SIP)". TechTarget.
- ↑ RFC 4168, The Stream Control Transmission Protocol (SCTP) as a Transport for the Session Initiation Protocol (SIP), IETF, The Internet Society (2005)
- ↑ William Stallings, p.209
- ↑ RFC 3986, Uniform Resource Identifiers (URI): Generic Syntax, IETF, The Internet Society (2005)
- ↑ Miikka Poikselkä et al. 2004.
- ↑ Brian Reid & Steve Goodman 2015.
- ↑ RFC 3581, An Extension to the Session Initiation Protocol (SIP) for Symmetric Response Routing, IETF, The Internet Society (2003)
- ↑ Azzedine (2006). Handbook of algorithms for wireless networking and mobile computing. CRC Press. p. 774. ISBN 978-1-58488-465-1.
- ↑ Porter, Thomas; Andy Zmolek; Jan Kanclirz; Antonio Rosela (2006). Practical VoIP Security. Syngress. pp. 76–77. ISBN 978-1-59749-060-3.
- ↑ "BlackBerry MVS Software". Na.blackberry.com. Retrieved 2011-01-11.
- ↑ "User-Agents We Have Known "VoIP User.org
- ↑ Stallings, p.214
- ↑ Stallings, pp.216-217
- ↑ James Wright. "SIP - An Introduction" (PDF). Konnetic. Retrieved 2011-01-11.
- ↑ Experiences of Using TTCN-3 for Testing SIP and also OSP Archived March 30, 2014, at the Wayback Machine.
- ↑ "Performance and Stress Testing of SIP Servers, Clients and IP Networks". StarTrinity. 2016-08-13.
- ↑ Jonsson, Lars; Mathias Coinchon (2008). "Streaming audio contributions over IP" (PDF). EBU Technical Review. Retrieved 2010-12-27.
- ↑ "JAIN SIP project". Retrieved 2011-07-26.
- ↑ "RFC3372: SIP-T Context and Architectures". September 2002. Retrieved 2011-01-11.
- ↑ White Paper: "Why SIP-I? A Switching Core Protocol Recommendation"
Bibliography
- Brian Reid; Steve Goodman (22 January 2015), Exam Ref 70-342 Advanced Solutions of Microsoft Exchange Server 2013 (MCSE), Microsoft Press, p. 24, ISBN 978-0-73-569790-4
- Miikka Poikselkä; Georg Mayer; Hisham Khartabil; Aki Niemi (19 November 2004), The IMS: IP Multimedia Concepts and Services in the Mobile Domain, John Wiley & Sons, p. 268, ISBN 978-0-47-087114-0