Delimiter
A delimiter is a sequence of one or more characters used to specify the boundary between separate, independent regions in plain text or other data streams.[1] An example of a delimiter is the comma character, which acts as a field delimiter in a sequence of comma-separated values.
Delimiters represent one of various means to specify boundaries in a data stream. Declarative notation, for example, is an alternate method that uses a length field at the start of a data stream to specify the number of characters that the data stream contains.[2]
Overview
Delimiters can be broken down into:
- Field and record delimiters; and
- Bracket delimiters.
Field and record delimiters
Field delimiters separate data fields. Record delimiters separate groups of fields.[3]
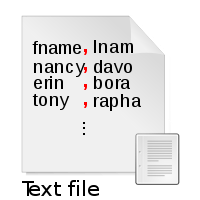
For example, the CSV file format uses a comma as the delimiter between fields, and an end-of-line indicator as the delimiter between records. For instance:
fname,lname,age,salary
nancy,davolio,33,$30000
erin,borakova,28,$25250
tony,raphael,35,$28700
specifies a simple flat file database table using the CSV file format.
Bracket delimiters
Bracket delimiters (also called block delimiters, region delimiters or balanced delimiters) mark both the start and end of a region of text.[4][5]
Common examples of bracket delimiters include:[6]
| Delimiters | Description |
|---|---|
( and ) |
Parentheses. The Lisp programming language syntax is cited as recognizable primarily by its use of parentheses.[7] |
{ and } |
Braces (also called curly brackets.[8]) |
[ and ] |
Brackets (commonly used to denote a subscript) |
< and > |
Angle brackets.[9] |
" and " |
commonly used to denote string literals.[10] |
' and ' |
commonly used to denote character literals.[10] |
<? and ?> |
used to indicate XML processing instructions.[11] |
/* and */ |
used to denote comments in some programming languages.[12] |
<% and %> |
used in some web templates to specify language boundaries. These are also called template delimiters.[13] |
Conventions
Computing platforms historically use certain delimiters by convention.[14] The following tables depict just a few examples for comparison.
Programming languages (See also, Comparison of programming languages (syntax)).
| String Literal | End of Statement | |
|---|---|---|
| Pascal | singlequote | semicolon |
| C | doublequote, singlequote | semicolon |
Field and Record delimiters (See also, ASCII, Control character).
| End of Field | End of Record | End of File | |
|---|---|---|---|
| Unix, Mac OS X, Amiga OS | Tab | LF | none |
| Windows, MS-DOS, OS/2, CP/M | Tab | CRLF | Control-Z[15] |
| Classic Mac OS, AppleDOS, ProDOS, GS/OS | Tab | CR | none |
| ASCII/Unicode | UNIT SEPARATOR Position 31 (U+001F) | RECORD SEPARATOR Position 30 (U+001E) | FILE SEPARATOR Position 28 (U+001C) |
Delimiter collision
Delimiter collision is a problem that occurs when an author or programmer introduces delimiters into text without actually intending them to be interpreted as boundaries between separate regions.[3][16] In the case of XML, for example, this can occur whenever an author attempts to specify an angle bracket character. In most file types there is both a field delimiter and a record delimiter, both of which are subject to collision. In the case of comma-separated values files, for example, field collision can occur whenever an author attempts to include a comma as part of a field value (e.g., salary = "$30,000"), and record delimiter collision would occur whenever a field contained multiple lines. Both record and field delimiter collision occur frequently in text files.
In some contexts, a malicious user or attacker may seek to exploit this problem intentionally. Consequently, delimiter collision can be the source of security vulnerabilities and exploits. Malicious users can take advantage of delimiter collision in languages such as SQL and HTML to deploy such well-known attacks as SQL injection and cross-site scripting, respectively.
Solutions
Because delimiter collision is a very common problem, various methods for avoiding it have been invented. Some authors may attempt to avoid the problem by choosing a delimiter character (or sequence of characters) that is not likely to appear in the data stream itself. This ad hoc approach may be suitable, but it necessarily depends on a correct guess of what will appear in the data stream, and offers no security against malicious collisions. Other, more formal conventions are therefore applied as well.
ASCII delimited text
The ASCII and Unicode character sets were designed to solve this problem by the provision of non-printing characters that can be used as delimiters. These are the range from ASCII 28 to 31.
| ASCII # | Unicode Name | Common Name | Usage |
|---|---|---|---|
| 28 | INFORMATION SEPARATOR FOUR | file separator (FS) | End of file. Or between a concatenation of what might otherwise be separate files. |
| 29 | INFORMATION SEPARATOR THREE | group separator (GS) | Between sections of data. Not needed in simple data files. |
| 30 | INFORMATION SEPARATOR TWO | record separator (RS) | End of a record or row. |
| 31 | INFORMATION SEPARATOR ONE | unit separator (US) | Between fields of a record, or members of a row. |
The use of ASCII 31 Unit separator as a field separator and ASCII 30 Record separator solves the problem of both field and record delimiters that appear in a text data stream.[17]
Escape character
One method for avoiding delimiter collision is to use escape characters. From a language design standpoint, these are adequate, but they have drawbacks:
- text can be rendered unreadable when littered with numerous escape characters, a problem referred to as leaning toothpick syndrome (due to use of \ to escape / in Perl regular expressions, leading to sequences such as "\/\/");
- text becomes difficult to parse through regular expression
- they require a mechanism to "escape the escapes" when not intended as escape characters; and
- although easy to type, they can be cryptic to someone unfamiliar with the language.[18]
- they do not protect against injection attacks
Escape sequence
Escape sequences are similar to escape characters, except they usually consist of some kind of mnemonic instead of just a single character. One use is in string literals that include a doublequote (") character. For example in Perl, the code:
print "Nancy said \x22Hello World!\x22 to the crowd."; ### use \x22
produces the same output as:
print "Nancy said \"Hello World!\" to the crowd."; ### use escape char
One drawback of escape sequences, when used by people, is the need to memorize the codes that represent individual characters (see also: character entity reference, numeric character reference).
Dual quoting delimiters
In contrast to escape sequences and escape characters, dual delimiters provide yet another way to avoid delimiter collision. Some languages, for example, allow the use of either a single quote (') or a double quote (") to specify a string literal. For example, in Perl:
print 'Nancy said "Hello World!" to the crowd.';
produces the desired output without requiring escapes. This approach, however, only works when the string does not contain both types of quotation marks.
Padding quoting delimiters
In contrast to escape sequences and escape characters, padding delimiters provide yet another way to avoid delimiter collision. Visual Basic, for example, uses double quotes as delimiters. This is similar to escaping the delimiter.
print "Nancy said ""Hello World!"" to the crowd."
produces the desired output without requiring escapes. Like regular escaping it can, however, become confusing when many quotes are used. The code to print the above source code would look more confusing:
print "print ""Nancy said """"Hello World!"""" to the crowd."""
Configurable alternate quoting delimiters
In contrast to dual delimiters, multiple delimiters are even more flexible for avoiding delimiter collision.[19]
For example, in Perl:
print qq^Nancy doesn't want to say "Hello World!" anymore.^; print qq@Nancy doesn't want to say "Hello World!" anymore.@; print qq(Nancy doesn't want to say "Hello World!" anymore.);
all produce the desired output through use of quote operators, which allow any convenient character to act as a delimiter. Although this method is more flexible, few languages support it. Perl and Ruby are two that do.[20][21]
Content boundary
A content boundary is a special type of delimiter that is specifically designed to resist delimiter collision. It works by allowing the author to specify a sequence of characters that is guaranteed to always indicate a boundary between parts in a multi-part message, with no other possible interpretation.[22]
The delimiter is frequently generated from a random sequence of characters that is statistically improbable to occur in the content. This may be followed by an identifying mark such as a UUID, a timestamp, or some other distinguishing mark. Alternatively, the content may be scanned to guarantee that a delimiter does not appear in the text. This may allow the delimiter to be shorter or simpler, and increase the human readability of the document. (See e.g., MIME, Here documents).
Whitespace or indentation
Some programming and computer languages allow the use of whitespace delimiters or indentation as a means of specifying boundaries between independent regions in text.[23]
Regular expression syntax
In specifying a regular expression, alternate delimiters may also be used to simplify the syntax for match and substitution operations in Perl.[24]
For example, a simple match operation may be specified in Perl with the following syntax:
$string1 = 'Nancy said "Hello World!" to the crowd.'; # specify a target string
print $string1 =~ m/[aeiou]+/; # match one or more vowels
The syntax is flexible enough to specify match operations with alternate delimiters, making it easy to avoid delimiter collision:
$string1 = 'Nancy said "http://Hello/World.htm" is not a valid address.'; # target string
print $string1 =~ m@http://@; # match using alternate regular expression delimiter
print $string1 =~ m{http://}; # same as previous, but different delimiter
print $string1 =~ m!http://!; # same as previous, but different delimiter.
Here document
A Here document allows the inclusion of arbitrary content by describing a special end sequence. Many languages support this including PHP, bash scripts and perl. A here document starts by describing what the end sequence will be and continues until that sequence is seen at the start of a new line.[25]
Here is an example in perl:
print <<ENDOFHEREDOC;
It's very hard to encode a string with "certain characters".
Newlines, commas, and other characters can cause delimiter collisions.
ENDOFHEREDOC
This code would print:
It's very hard to encode a string with "certain characters". Newlines, commas, and other characters can cause delimiter collisions.
By using a special end sequence all manner of characters are allowed in the string.
ASCII armor
Although principally used as a mechanism for text encoding of binary data, ASCII armoring is a programming and systems administration technique that also helps to avoid delimiter collision in some circumstances.[26][27] This technique is contrasted from the other approaches described above because it is more complicated, and therefore not suitable for small applications and simple data storage formats. The technique employs a special encoding scheme, such as base64, to ensure that delimiter characters do not appear in transmitted data.
This technique is used, for example, in Microsoft's ASP.NET web development technology, and is closely associated with the "VIEWSTATE" component of that system.[28]
Example
The following simplified example demonstrates how this technique works in practice.
The first code fragment shows a simple HTML tag in which the VIEWSTATE value contains characters that are incompatible with the delimiters of the HTML tag itself:
<input type="hidden" name="__VIEWSTATE" value="BookTitle:Nancy doesn't say "Hello World!" anymore." />
This first code fragment is not well-formed, and would therefore not work properly in a "real world" deployed system.
In contrast, the second code fragment shows the same HTML tag, except this time incompatible characters in the VIEWSTATE value are removed through the application of base64 encoding:
<input type="hidden" name="__VIEWSTATE" value="Qm9va1RpdGxlOk5hbmN5IGRvZXNuJ3Qgc2F5ICJIZWxsbyBXb3JsZCEiIGFueW1vcmUu" />
A third code fragment shows the same HTML tag, except this time incompatible characters in the VIEWSTATE value are removed through the application of percent-encoding:
<input type="hidden" name="__VIEWSTATE" value="BookTitle:Nancy%20doesn%27t%20say%20%22Hello%20World!%22%20anymore." />
This prevents delimiter collision and ensures that incompatible characters will not appear inside the HTML code, regardless of what characters appear in the original (decoded) text.[28]
See also
References
- ↑ Federal Standard 1037C - Telecommunications: Glossary of Telecommunication Terms
- ↑ Rohl, Jeffrey S. (1973). Programming in Fortran. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-7190-0555-8. describing the method in Hollerith notation under the Fortran programming language.
- 1 2 de Moor, Georges J. (1993). Progress in Standardization in Health Care Informatics. IOS Press. ISBN 90-5199-114-2. p. 141
- ↑ Friedl, Jeffrey E. F. (2002). Mastering Regular Expressions: Powerful Techniques for Perl and Other Tools. O'Reilly. ISBN 0-596-00289-0. p. 319
- ↑ Scott, Michael Lee (1999). Programming Language Pragmatics. Morgan Kaufmann. ISBN 1-55860-442-1.
- ↑ Wall; Larry; Jon Orwant (July 2000). Programming Perl (Third ed.). O'Reilly. ISBN 0-596-00027-8.
- ↑ Kaufmann, Matt (2000). Computer-Aided Reasoning: An Approach. Springer. ISBN 0-7923-7744-3.p. 3
- ↑ Meyer, Mark (2005). Explorations in Computer Science. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-7637-3832-7. references C-style programming languages prominently featuring curly brackets and semicolons.
- ↑ Dilligan, Robert (1998). Computing in the Web Age. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-306-45972-6.Describes syntax and delimiters used in HTML.
- 1 2 Schwartz, Randal (2005). Learning Perl. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-596-10105-3.Describes string literals.
- ↑ Watt, Andrew (2003). Sams Teach Yourself Xml in 10 Minutes. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-672-32471-0. Describes XML processing instruction. p. 21.
- ↑ Cabrera, Harold (2002). C# for Java Programmers. Oxford Oxfordshire: Oxford University Press. ISBN 978-1-931836-54-8. Describes single-line and multi-line comments. p. 72.
- ↑ "Smarty Template Documentation". Retrieved 2010-03-12. See e.g., Smarty template system documentation, "escaping template delimiters".
- ↑ International Organization for Standardization (December 1, 1975). "The set of control characters for ISO 646". Internet Assigned Numbers Authority Registry. Alternate U.S. version: . Accessed August 7, 2005.
- ↑ Lewine, Donald (1991). Posix Programmer's Guide. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-937175-73-6. Describes use of control-z. p. 156,
- ↑ Friedl, Jeffrey (2006). Mastering Regular Expressions. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-596-52812-6. describing solutions for embedded-delimiter problems p. 472.
- ↑ Discussion on ASCII Delimited Text vs CSV and Tab Delimited
- ↑ Kahrel, Peter (2006). Automating InDesign with Regular Expressions. O'Reilly. ISBN 0-596-52937-6.p. 11
- ↑ Wall; Larry; Jon Orwant (July 2000). Programming Perl (Third ed.). O'Reilly. p. 63. ISBN 0-596-00027-8.
- ↑ Wall; Larry; Jon Orwant (July 2000). Programming Perl (Third ed.). O'Reilly. p. 62. ISBN 0-596-00027-8.
- ↑ Yukihiro, Matsumoto (2001). Ruby in a Nutshell. O'Reilly. ISBN 0-596-00214-9. In Ruby, these are indicated as general delimited strings. p. 11
- ↑ Javvin Technologies, Incorporated (2005). Network Protocols Handbook. Javvin Technologies Inc. ISBN 0-9740945-2-8. p. 26
- ↑ 200, Cicling (2001). Computational Linguistics and Intelligent Text Processing. Oxford Oxfordshire: Oxford University Press. ISBN 978-3-540-41687-6. Describes whitespace delimiters. p. 258.
- ↑ Friedl, Jeffrey (2006). Mastering Regular Expressions. Oxford Oxfordshire: Oxford University Press. ISBN 978-0-596-52812-6. page 472.
- ↑ Perl operators and precedence
- ↑ Rhee, Man (2003). Internet Security: Cryptographic Principles, Algorithms and Protocols. John Wiley and Sons. ISBN 0-470-85285-2.(an example usage of ASCII armoring in encryption applications)
- ↑ Gross, Christian (2005). Open Source for Windows Administrators. Charles River Media. ISBN 1-58450-347-5.(an example usage of ASCII armoring in encryption applications)
- 1 2 Kalani, Amit (2004). Developing and Implementing Web Applications with Visual C# . NET and Visual Studio . NET. Que. ISBN 0-7897-2901-6.(describes the use of Base64 encoding and VIEWSTATE inside HTML source code)