Christopher Hadnagy
Christopher James Hadnagy (born Summer of 1973) is an American security consultant, author, and professional social engineer. He is most well known for creating the world’s first framework for social engineering (SE) and authoring one of the first books in the field of social engineering, Social Engineering: The Art of Human Hacking.[1] He is the Chief Human Hacker of Social-Engineer, Inc., which performs security audits to uncover the weaknesses in an organization’s human network through real world social engineering penetration tests (pentests).
Hadnagy specializes in understanding how malicious attackers exploit human communication and trust to obtain access to information and resources through manipulation and deceit.[2] His goal is to secure companies by educating their employees on the methods used by attackers, identifying vulnerabilities, and mitigating issues through appropriate levels of awareness and security.[3]
Hadnagy is also the father of Amaya Hadnagy, the owner of Youtube Channel TeenyTinyTubers. His 12 year old daughter was also the SE Village Photographer during DefCon 24 .
Early life
Hadnagy moved around frequently in his early life, spending many years in New York, Pennsylvania and Florida.
While attending a college on the West-coast of Florida for a degree in programming, Hadnagy became interested in emerging Internet technology and wrote a simple script (now called War Dialers) that linked together two 9600 baud modems to call random numbers at the telephone company and play a tone; the experiment shut down the numbers. He later found that a number of phone lines in that county had been shut down for a short periods of time by this script. This experiment began Hadnagy’s interest in learning more about how computer technology and the Internet work.
He was also an internal negotiator for the purchase of stainless steel in the countries of China and India; during which time, he brokered a deal with one of China’s largest stainless steel mills that was the first of its kind in American history.
Professional SE career
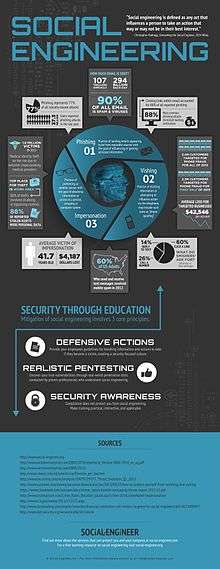
Hadnagy began his technical career with his own business, AREESA Computers, making and repairing home and business computers under the tagline “Your computer company of the future.” After personal PC’s became significantly less expensive, he moved to doing more networking and vulnerability scanning services with his company, under the new name White Hat Defense. It was at this time, Hadnagy worked with the team that created BackTrack (now Kali) and the mastermind behind that, Mati, was a mentor and friend. Mati nurtured Hadnagy’s skill set in social engineering. Hadnagy commented, “I guess I was always an SE but never knew it…”[4]
While contracting with Offensive Security as their Operations Manager, Hadnagy saw a gap in the field of Information Security and started to write a five-day course that outlined the principles of how to be a social engineer. After determining that there was very little published information on SE geared to serious security professionals on the web, Hadnagy sought like-minded social-engineers in the InfoSec community. This resulted in a small band of people coming together to formulate the Social-Engineer Framework, which after nine months of hard work, was published at www.social-engineer.org. Along with the framework, the initial core team launched monthly newsletters, podcasts, and blog posts.
After the launch of the framework, Kevin Mitnick’s publisher contracted Hadnagy to write a formal “how-to” manual based on his framework for social engineering. In 2011, Social Engineering: The Art of Human Hacking was published by Wiley Publishing, Inc.
After Social Engineering was published, Hadnagy began to receive calls from companies wanting assistance with setting up SE pentests and training in SE. To accommodate the number of clients requesting these specialized services, Hadnagy launched his present company, Social-Engineer, Inc., with a focus on pentesting the human element of corporate security and presenting a 5-day performance-based social engineering training course. Social Engineering, Inc. employees a team of psychology and social-engineering professionals, as well as researchers and technical staff who focus on security of human networks.
As Hadnagy was establishing himself and his company in the field of social engineering, he developed a friendship with psychologist Dr. Paul Ekman. Ekman coached Hadnagy in reading and using microexpressions, which quickly turned into a passion for Hadnagy. This relationship and passion lead to the release of Hadnagy’s second book, Unmasking the Social Engineer: The Human Side of Security, which was overseen by Dr. Paul Ekman and his associate, Paul Kelly. This second book is a combination of Ekman’s life’s work with Hadnagy’s own; written to build an understanding of how humans are influenced by nonverbal communication.
Over the years Hadnagy has presented and trained at events such as RSA,[5] Black Hat,[6] ISSA[7] and given various presentations for corporate and government clients.
Hadnagy is a certified Expert Level graduate of Dr. Paul Ekman’s Micro Expressions courses, having made the study of non-verbal behaviors one of his specialties. In addition, he holds certifications as an Offensive Security Certified Professional (OSCP) and an Offensive Security Wireless Professional (OSWP).[8]
History with DEF CON
At DEF CON 17 Hadnagy was approached to help start a professional, while entertaining, Social Engineering contest for the popular hacking conference, DEF CON.

Hadnagy founded the Social Engineering Capture the Flag (SECTF) competition based on the challenge of creatively and legally raising awareness of the threat SE poses to security. Ethical conduct is strictly enforced and personal/financial information is not allowed to be targeted.[9] Both business leaders and government agencies initially raised concern regarding the type of information that would be gathered and the methods that would be employed to collect it, however, after four years this has diminished as organizations have seen the rules of the contest and its results.[10]
The contest is broken down into two sections: first, information gathering and planning attack vectors in the month before DEF CON and second, a public execution of a vishing attack in the SEVillage at DEF CON.[11] A detailed competition report is released each year which many businesses utilize to help improve their security awareness programs. The SECTF has also researched and reported on the topics of gender in the SE field (showing that women make just as good, if not better, SE’s than men), which industries are most susceptible to SE attacks, and improvements that have been seen in companies successfully targeted in previous years.
At DEF CON 18 Hadnagy and crew launched the first SECTF which broke 18 years of DEF CON history when it became the first contest to receive a black badge its first year. Each year the contest has grown in popularity and size.[12]
In 2011, Hadnagy developed SECTF4Kids for DEF CON 19, which is an event designed to help children learn to use critical thinking skills to solve puzzles, crack ciphers and race other teams against the clock. The SECTF4Kids was created with the intention of teaching younger generations that “social engineering skills can be used for good, that critical thinking is important, and that you can learn to influence others, read body language, pick locks and GET PAID to do it.”[13] The kids contest has a different theme each year but always includes lock picking, solving ciphers, and basic information gathering through the process of objective analysis of information presented. In 2014 the SECTF4Kids was made an official DEF CON event rather than one of the kid’s events.[14]
References
- ↑ Chereshnev, Evgeny. "The Best-Selling Books on Security from RSA 2014". KaperskyLab Daily. Retrieved February 2014. Check date values in:
|access-date=(help) - ↑ "Elaborate Iranian hacking scheme targets US lawmakers". ITnews. Retrieved May 30, 2014.
- ↑ "HR a Hot Target for Cybercriminals". eSecurity Planet. Retrieved June 3, 2014.
- ↑ "Reddit, IAmA with Chris Hadnagy". Reddit, subforum IAmA.
- ↑ RSA http://www.rsaconference.com/speakers/chris-hadnagy. Retrieved June 4, 2014. Missing or empty
|title=(help) - ↑ BlackHat https://www.blackhat.com/html/bh-us-12/training/courses/bh-us-12-training_social-engineering.html. Retrieved June 4, 2014. Missing or empty
|title=(help) - ↑ "8th Annual Charlotte ISSA Security Summit". ISSA Charlotte Metro. Retrieved 22 July 2014.
- ↑ "Social-Engineer, Inc. _About page". Social-Engineer, Inc. Retrieved 4 May 2015.
- ↑ "Social-Engineer.Org CTF Update – Awareness Abounds". Security through Education. July 21, 2010. Retrieved 25 July 2014.
- ↑ Jackson Higgins, K. (6/4/2010). "Defcon To Host 'Capture The Flag' Social Engineering Contest No unethical activities or 'damage' to targeted companies or people allowed". InformationWeek: DARKreading. Retrieved 25 July 2014. Check date values in:
|date=(help) - ↑ "The Social Engineering CTF – How Strong is Your Schmooze". Security through Education. Retrieved 25 July 2014.
- ↑ Smith, Mrs. "Social engineer tag teams to capture the flags at Def Con 22 contest". NetworkWorld. Retrieved 4 May 2015.
- ↑ "What the SECTF4Kids is All About". Security through Education. Retrieved 25 July 2014.
- ↑ "Kids To Hack Corporate Crime Caper Case At DEF CON". InformationWeekly: DARKreading. Retrieved 25 July 2014.
Bibliography
Books
- Social Engineering: The Art of Human Hacking (Wiley Publishing, Inc., 2011) ISBN 978-0-470-63953-5
- Unmasking the Social Engineer: The Human Element of Security.(Wiley, 2014) ISBN 978-1-118-60857-9
- Phishing Dark Waters: The Offensive and Defensive Sides of Malicious Emails.(Wiley, 2015) ISBN 978-1-118-95847-6
Print/online articles
- Pentest Magazine, Special SE edition 09/2012
- "Neuro-Linguistic Hacking"
- "The Top Five Social Engineering Mitigiation Tips"
- The Ethical Hacker Network, regular monthly column January through September, 2012
- "Top 5 Tips To Make Social Engineering Your Career"
- "Look Mom, I’m a Thespian: How to Use Acting Skills as a Social Engineer"
- "Scam Your Clients for Their Own Good"
- "Bringing the Unsexy Back: The Process of Selling SE Penetration Tests"
- "An Insider’s Look at the Social-Engineer.Org SE CtF at DEFCON"
- "Nonverbal Human Hacking"
- "Social-Engineer.org is Vegas Bound Baby!"
- "Social Engineering as a Technical Tool"
Audio/podcasts
- Social-Engineer.org podcast series at Social-Engineer.org
External links
- www.social-engineer.org Security Through Education, free online resource on social engineering
- www.social-engineer.com Social-Engineer, Inc. corporate website
- Social-Engineer, vimeo channel
- SocialEngineerOrg, YouTube channel
Print/online interviews
- Barker, T. (July 1, 2014)4 Powerful Things Con Men Can Teach You About Persuasion. Time Online.
- Lu, Y. (June 27, 2014) 5 Things Hackers Don't Want You to Know: Social engineer Chris Hadnagy gives suggestions on how to protect online safety from a hacker's perspective. INC.
- Reddit, IAmA with Chris Hadnagy (June 26, 2014) IAmA professional Social Engineer
- The Economist. (July 12, 2014) Digital Disease Control
- Jackson-Higgins, K. (June, 2014) Kids To Hack Corporate Crime Caper Case At DEF CON. InformationWeek: DARKReading.
- Armerding, T. (June 5, 2014) 5 summer scams to watch out for this season. CSO.
- Robb, D. (June 3, 2014). HR a Hot Target for Cybercriminals. eSecurityPlanet.
- Finkle, J. (May, 2014). Iranian hackers use fake Facebook accounts to spy on U.S., others. REUTERS.
- Collett, S. (April 21, 2014). Four of the newest (and lowest) Social Engineering scams. CSO.
- Slater, D. (April 2, 2014). 3 smarter ways to fight social engineering. FierceITSecurity.
- Burgess, C. (April 10, 2014). The Security Threat Posed by Social Engineering. RSAConference.
- Jackson Higgins, K. (April 7, 2014). Social Engineering Grows Up. InformationWeek: DARKreading.
- Rothke, B. (April, 2014). Unmasking the Social Engineer: The Human Element of Security. RSAConference.
- Slater, D. (March 31, 2014). Social engineering: A short glossary of terms 13 social engineering phrases and lingo, defined with help from Chris Hadnagy. FierceITSecurity.
- Ark, R. (October, 2013). Protecting Against Social Engineering: An Interview with Christopher Hadnagy. HackSurfer
- Storm, D. (October 30, 2013). Free candy: Social engineer tricks for company secret treats. ComputerWorld.
- Kim, Q. (September 6, 2013). Social engineering: The human story behind hacking. NPR: Marketplace.
- Ragan, S. (September 4, 2013). Aggressive social engineering campaign uncovered in Europe. CSO.
- Ragan, S. (Aug 5, 2013). DEF CON attendees demonstrate social engineering prowess in CTF contest. CSO.
- Goodchild, J. (April, 2013) Social engineering in penetration tests: 6 tips for ethical (and legal) use. CSO.
Audio/video interviews
- PDC cast. (June, 2014). Podcast episode377 – Interview with chris “loganWHD” hadnagy. Security Weekly. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/.
- Webb, A. (March 2014). RSA 2014 chris hadnagy human hacking & non verbal communication. SecureNinjaTV. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/.
- Dean, M. (January, 2014). Will the target breach cause more SE havoc? FoxBusiness: Firewall. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/.
- Dean, M. (January, 2014). The target breach and the SE implications. FoxBusiness: Firewall. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/.
- Caine, P. (November, 2013). Cyber Security. Chicago Tonight. Retrieved from http://chicagotonight.wttw.com/2013/11/19/cyber-security
- Kim, Q. (September 6, 2013). Social engineering: The human story behind hacking (Print/Audio). NPR:Marketplace.
Presentations/speeches
- Hadnagy, C. and Fincher, M. (May 2014). Social engineering: When the phone is more dangerous than malware. RSA Conference. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/
- Chris Hadnagy presented “Social Engineering: The Art of Human Hacking” at a security seminar with partner Asgent in Tokyo Japan[1] on May 24, 2013.
- Hadnagy, C. (February, 2012). Human Hacking Exposed. RSA Conference. Retrieved from http://www.social-engineer.com/social-engineer-news-videos/
- ↑ "Asgent Announces "Evolving Targeted Attacks and the Reality Behind Human Hacking" Seminar - Learn about social engineering from leaders in the field -". Asgent, Inc. Retrieved 13 June 2014.